The recently disclosed remote code execution vulnerability in Apache Log4j2, a Java-based logging component, has caused significant impact worldwide. This component is used extensively in business system development to record logging information about program input and output, and is extremely widely used. In most cases, developers write error messages caused by user input to the log.
The sudden disclosure of this vulnerability has not only caused developers using Log4j2 to “fix” the problem overnight, but also caught the framework maintainers off guard. Volkan Yazıcı is a PMC member of the Apache Software Foundation Logging Services. According to his description, since the vulnerability was made public, the maintainers have been busy mitigating the vulnerability, as well as fixing bugs, documentation, and CVEs, while responding to queries from others. But even so, they have been subjected to a lot of harsh criticism and even rebuke - even if it is unpaid work.
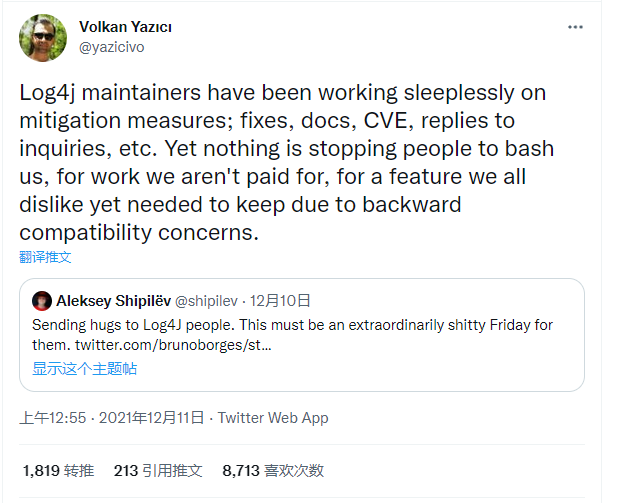
Volkan also mentions that the old feature that caused the vulnerability was actually intended to be removed (the vulnerability was essentially a JNDI injection into the lookup method of Log4j2), but was left in place to ensure backward compatibility.
Of course, there are those who disagree with Volkan’s “backwards compatibility” principle. He said that if the development team wants to remove old features, they don’t need to hesitate and just do what they want. If the people who use it think it’s important, they can fork the project and maintain it themselves – at their own cost in time, effort, and money.
As an open source underlying component, Log4j2 is used by a number of very large Internet companies, such as Google, Apple, and Amazon. As you can see from the comments on Volkan’s tweets, many people said they just learned that these high-cap, high-profit companies don’t put any support into this underlying component, and even the maintainers are paid nothing.
Reference https://www.oschina.net/news/173273/log4j-maintainer-response