Recently, I want to open up the user relationship of several applications and get a centralized user management system to unify the user system of the application. After some research, I selected Red Hat’s open source Keycloak, which is a very powerful unified authentication authorization management platform. The reason why Keycloak was selected is based on the following reasons.
Ease of Use
Keycloak provides a one-stop single sign-on solution for web applications and Restful services. Its goal is to make application security management easy, so that developers can easily secure their applications and services. And Keycloak provides a visual management interface for login, registration, and user management, with which you can configure security policies that meet your needs and perform user management.
Powerful Features
Keycloak implements the industry’s common authentication authorization protocols and common security technologies, mainly.
- Single Sign-On (SSO) for browser applications.
- OIDC authentication authorization.
- OAuth 2.0.
- SAML.
- Multi-tenant support.
- Identity Proxy - Authentication using an external OpenID Connect or SAML identity provider.
- Third-party login.
- User Federation - Synchronize users from LDAP and Active Directory servers.
- Kerberos Bridge - Automatically authenticate users logging into Kerberos servers.
- Management console for centralized management of users, roles, role mappings, clients, and configurations.
- Management Console for centralized management of user accounts.
- Customizable Topic.
- Two-stage authentication.
- Full login process - optional user self-registration, password recovery, verifying email, requesting password updates, etc.
- Session Management - Administrators and users themselves can view and manage user sessions.
- Token Mapping - Map user attributes, roles, etc. to tokens and statements.
- Security policy recovery functionality.
- CORS support - Client adapter has built-in support for CORS.
- Custom SPI interface extensions.
- Client adapters for JavaScript applications, WildFly, JBoss EAP, Fuse, Tomcat, Jetty, Spring, etc.
- Support for any platform/language with the OpenID Connect Relying Party library or SAML 2.0 Service Provider library.
And there is a dedicated Spring Boot Starter that is very easy to integrate into Spring Boot.
Practice-based open source
Red Hat’s products are the best. Red Hat’s good reputation determines the reliability of Keycloak. It follows the Apache 2.0 open source protocol for open source, and after eight years of continuous open source, the code is of high quality and ideal for custom development. Red Hat’s commercial paid authentication licensing product, Red Hat SSO, is based on Keycloak. It provides a dynamic single sign-on solution for enterprises, indirectly proving Keycloak’s reliability.
Adaptation to Spring Security
This framework is adapted for Spring Security and Spring Boot and is ideal for migration extensions that use both systems. This is one of the key reasons why I chose it.
Disadvantages
Although the advantages are very many, the disadvantages are also obvious. Powerful means more complex architecture, more concepts and higher learning costs.
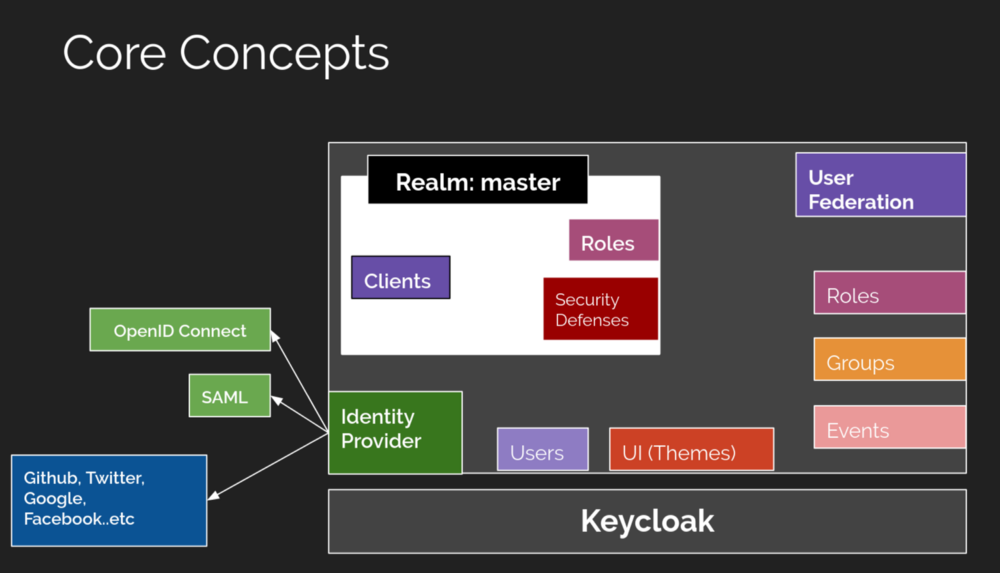
Another reason for the high learning cost is that there are few Chinese materials, so you need to read the official documentation yourself. For the business needs of the authentication method may need to implement some interfaces, the same test of personal coding skills.
Finally
I have been concerned about this thing for a long time but did not start, first because it is really challenging, the second no actual development scenarios, now the opportunity has come, today a simple introduction to this framework, so that people who do not understand it first simple understanding. If you have a detailed study and practice of Keycloak, you can basically handle the construction of some medium and large application security system, both tempting and challenging. In addition, this program is suitable for unified authentication authorization portal construction, not quite suitable for some small applications, relatively heavy. But microservices should be great with this. It is a good choice when the new Spring Authentication Server is not yet available for production.
Reference
https://felord.cn/intro-to-keycloak.html