While learning Spring Security did you have any of the following two questions.
- How is login configured in Spring Security?
- What is the access control mechanism for Spring Security?
SpringBootWebSecurityConfiguration
The answers to the above two questions are in the configuration class SpringBootWebSecurityConfiguration. You can follow this mind map to understand it.
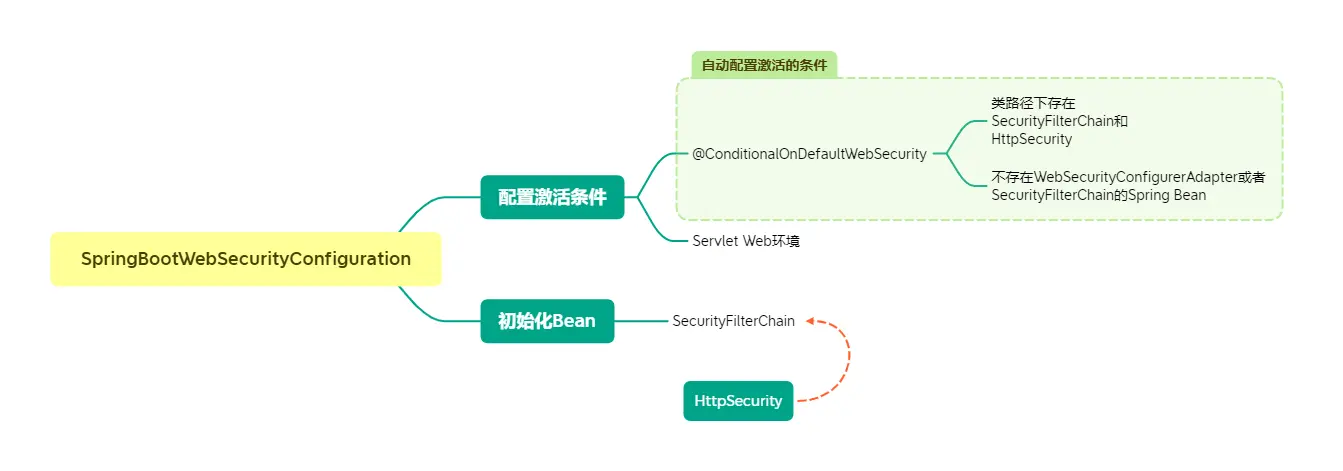
This auto-configuration: SpringBootWebSecurityConfiguration provides a default set of Spring Security configurations for Spring Boot applications.
The configuration here is that all requests must be initiated by an authenticated user, with form login and Http Basic Authentication enabled. This is what we need to do when we visit /foo/bar to be authenticated and to be able to log in to the form. This is our daily development needs to customize, in HttpSecurity related articles fat brother also explained. What is this SecurityFilterChain in the end?
SecurityFilterChain
From the above, we can see that HttpSecurity is a build class, and its mission is to build a SecurityFilterChain.
When a request HttpServletRequest enters SecurityFilterChain, the matches method is used to determine whether the conditions are met to enter the filter chain. It’s like you are a VIP taking the VIP channel and enjoying a series of VIP treatment; you are a normal user, you take the normal user channel and enjoy the normal user treatment.
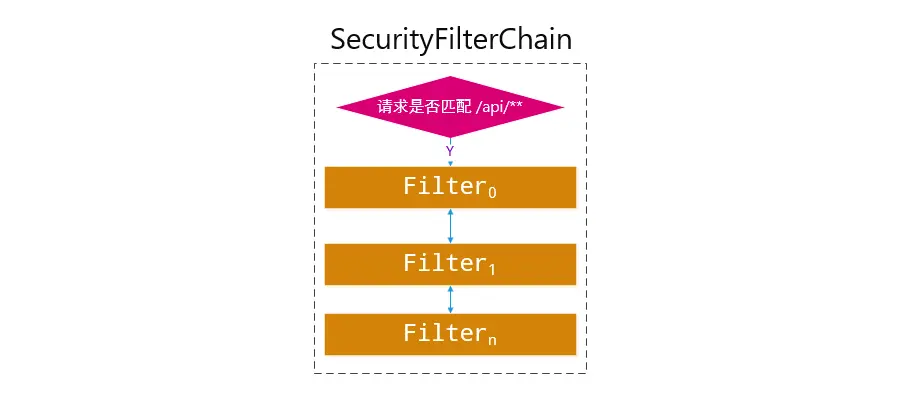
Regardless of the user’s role, there is a filter chain, and there are 1-n SecurityFilterChains in an application. So who manages multiple SecurityFilterChains?
Remember the formula
HttpSecurity ->SecurityFilterChain.
FilterChainProxy
FilterChainProxy is a GenericFilterBean (even if the Servlet Filter is a Spring bean) that manages all the SecurityFilterChain injected into the Spring IoC container. This is how I configured FilterChainProxy when I was new to Spring Security.
|
|
Different SecurityFilterChains are matched according to different request paths. The following is a diagram.
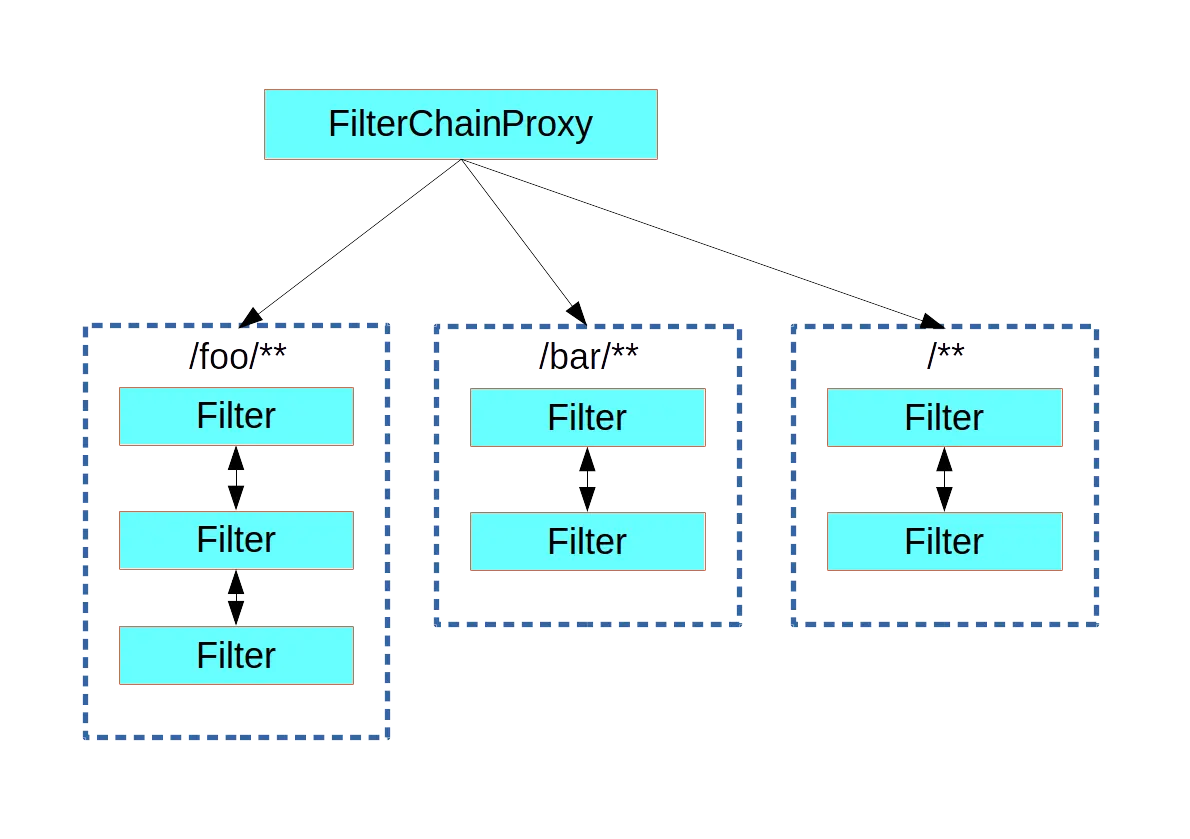
Later will also contact this class, now you just need to understand the above diagram on the line.
Note: Multiple instances of
FilterChainProxyare not recommended in the same filter chain, and should not be used as a mere filter; it should only take on the function of managing theSecurityFilterChain.
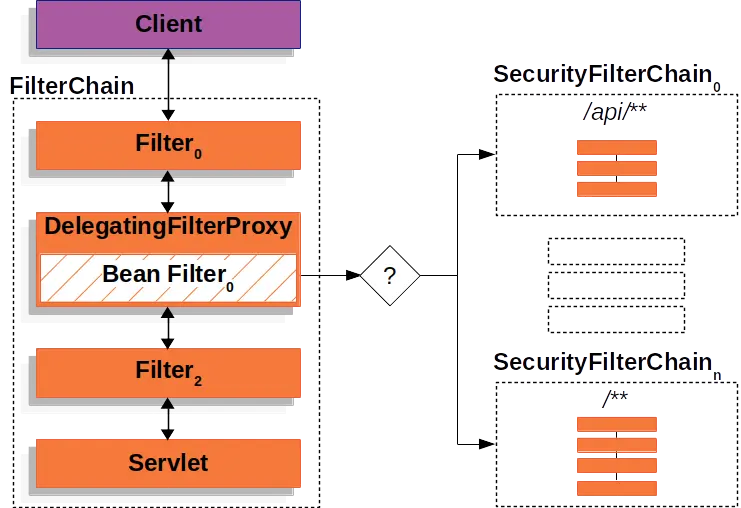
DelegatingFilterProxy
The Filter lifecycle does not match between the Servlet container and the Spring IoC container. In order for the Spring IoC container to manage the Filter lifecycle, the FilterChainProxy is delegated to the DelegatingFilterProxy under Spring Web. Also, FilterChainProxy does not call the standard Servlet filter lifecycle methods on any filter bean added to the application context, the FilterChainProxy lifecycle methods are delegated to DelegatingFilterProxy for execution. And DelegatingFilterProxy exists as a connector between Spring IoC and Servlet.
Brief summary
The above three concepts are very important and relate to the whole filter chain system of Spring Security. But as a beginner, it is very normal to understand as much as you can and not to get hung up on what you don’t understand because you can’t reach the level of learning at this stage. But when you are done with Spring Security, these concepts must be understood.
Reference
https://my.oschina.net/10000000000/blog/5438386