When using Keycloak, you may have noticed that user management is done through the UI provided by Keycloak, which is convenient but often not suitable for use in development. For example, you can’t let end-users go directly to Keycloak’s Admin Console to register. Therefore, it is necessary to APIize these functions, and today we are going to share a method to operate Keycloak through programming.
Introduction to Keycloak Admin Client
All our operations in Keycloak Admin Console have specific Restful APIs, which are collectively called Keycloak Admin REST API. The Keycloak Admin Client is a Java HTTP client wrapper for the Keycloak Admin REST API. We just need to introduce the following dependencies to integrate it.
Here is a brief mention , the underlying use of JBoss Rest Web Service client Resteasy . JBoss RESTEasy is a framework for developing RESTFul Web services using the Java language . It is an implementation of JAX-RS (Java API for RESTful Web Services) , some of its highlights :
- no configuration file , based on annotations and Java POJO you can implement RESTful client .
- Based on JBoss Seam (Java EE upper layer enhancements) programming model .
These only as extended knowledge , unless you deep customization , you do not need to learn it , because Keycloak Admin Client has shielded its steep learning costs , next let’s start using it .
Use of Keycloak Admin Client
The Keycloak Admin REST API is required to place an Bearer Token in the Authorization request header in the request. The access rights of the corresponding API are obtained according to the authority information carried in the Token. So when we use Keycloak Admin Client, we should pay special attention to whether the client you are currently using has access rights. The next example uses it as an example to register a new user.
Creating a new user using the Admin account
The Admin administrator in Master Realm has the highest privileges to manage Keycloak and can do almost anything he wants in Keycloak.
Declare a Keyclock instance according to our configuration.
|
|
Here the authorization method is Password Authorization, which requires that Direct Access Grants Enabled must be turned on under the Setting option of the client, which means that the admin-cli client can access the user’s username and password, and use them to obtain an access token from the Keycloak server, and then be able to perform further access authorization operations.
How can we register new users?
We can do it like this.
|
|
Here UserRepresentation is the user object, we define a user with the username apicreated and a non-temporary password 123456 and register it to Master Realm.
How do I know about these APIs?
The official documentation for the Admin API is given at the following address.
|
|
This is the documentation you must see to use the Keycloak Admin REST API.
Creating new users with Realm admin users
Master Realm admin accounts don’t bother with these “low-level” operations, so they are usually left to the “minions”. In order to create users in felord.cn Realm, you can give a Master Realm user a role manager-users that creates felord.cn users.
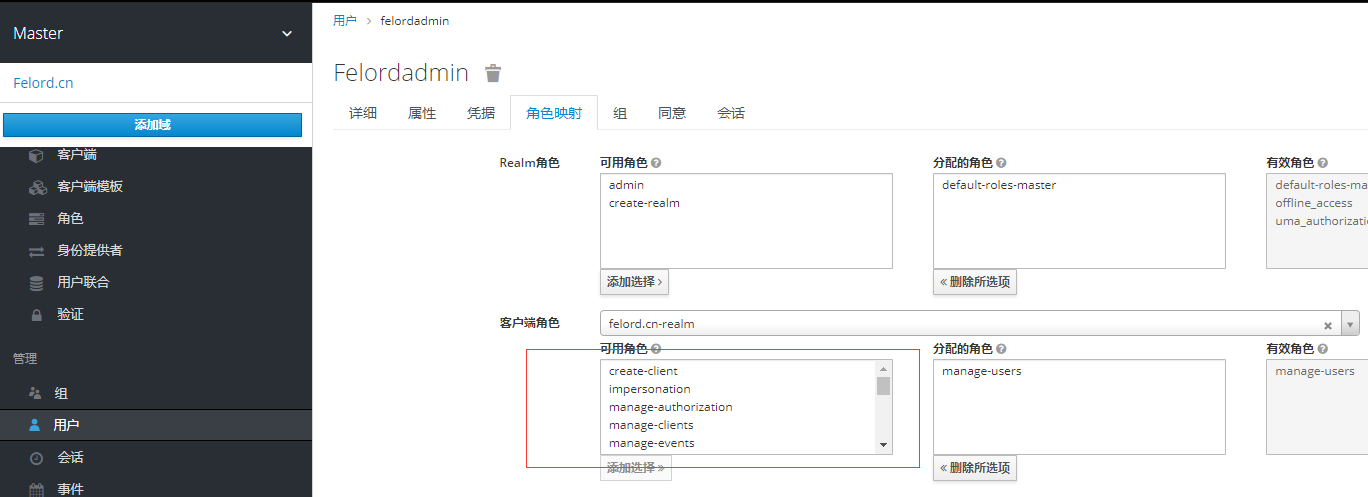
There are many more roles in the red box that you need to understand.
Creating a user for felord.cn using the Master account should be written like this.
|
|
Creating users with service accounts
Each Realm has a management client called realm-management, which is used to manage the current Realm, and you can enable the service account feature of realm-management by following the configuration below.
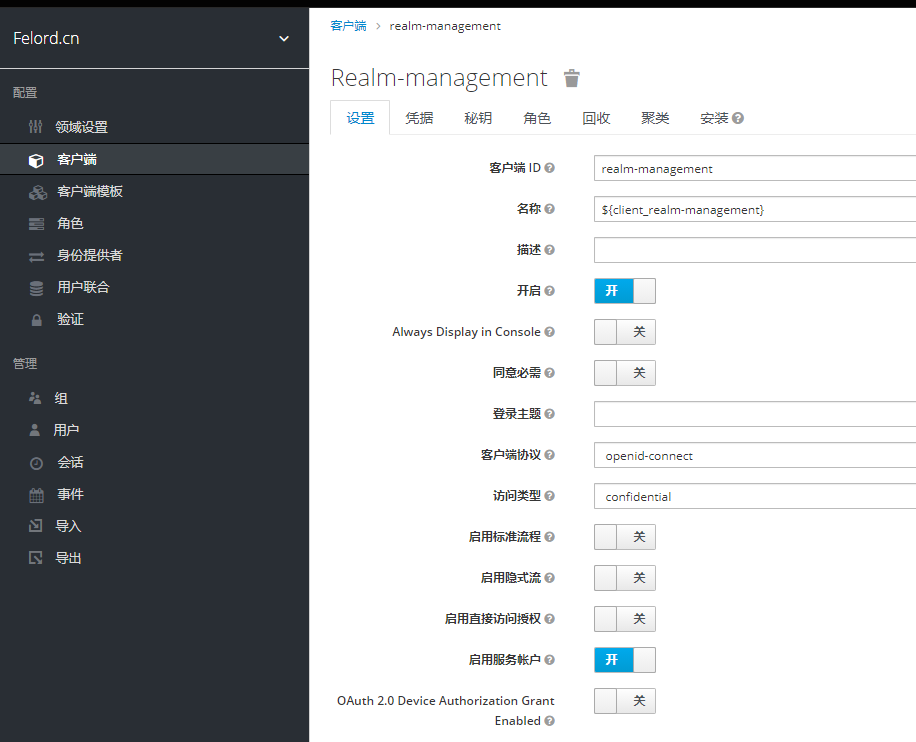
This way we can get the access credentials of realm-management directly from the Keycloak server, because realm-management has all the administrative functions, so we can create new users in the name of the client instead of the administrative user, and we are not limited to creating users.
Keycloak’s instantiation code is not quite the same as before.
The authorization mode here is different from user behavior, it is client behavior, so
grant_typeis changed to client mode.
Summary
Creating a user is the same as the previous two methods, you can create a user to try, and there are other APIs that can be implemented in this way. Today, we introduced how to call the Keycloak Admin REST API, which allows you to perform some administrative operations on Keycloak in code. It should be noted that these operations are closely related to the role of the subject of the current operation. There will be space later for a brief introduction to the administrative roles in Keycloak.
Reference
https://felord.cn/keycloak6.html