In the previous posts, I joined you for a cursory look at Keycloak. As I gradually learned more, I found that I entered a misunderstanding, originally I thought that the focus of Spring Security integration with Keycloak was on this aspect of Spring Security, in fact, I found that Keycloak has no room to work with several filters on Spring Security’s Adapter, perhaps it needs I think we need to understand Keycloak itself before we can have a breakthrough. So what I want to understand today is the Realm in Keycloak.
Realm
It is used to logically isolate some specific space, a bit of multi-tenancy, different Realm are isolated from each other, have their own characteristic configuration, do not affect each other.
When to use Realm
Realm is used when a specific number of users need to be isolated from each other, or when a series of services need to be managed in a unified way.
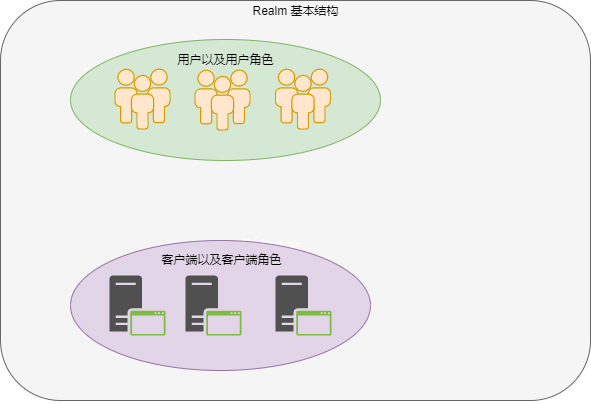
Let’s say we need to develop an application and deploy it with the domain name felord.cn. We can define a Realm with the name felord.cn to manage the roles, resources, and clients of the application, and the client development can focus on the business. The whole Keycloak is like an open platform to manage the lifecycle of Realm centrally, and these Realm can interoperate with each other under OIDC protocol.
Master Realm
If you have read my previous articles about Keycloak, you may remember that when you start Keycloak for the first time, you will come into contact with a Realm called Master, which is a Realm built into Keycloak and its role is somewhat similar to that of the root user in Linux, mainly for managing other Realms. The administrator account in the Realm has the right to view and manage any other Realm created on the Keycloak server instance.
And you will find that the realm created by Master Realm is actually a client of Master Realm, even it is its own client, and the name follows <realm name>-realm.
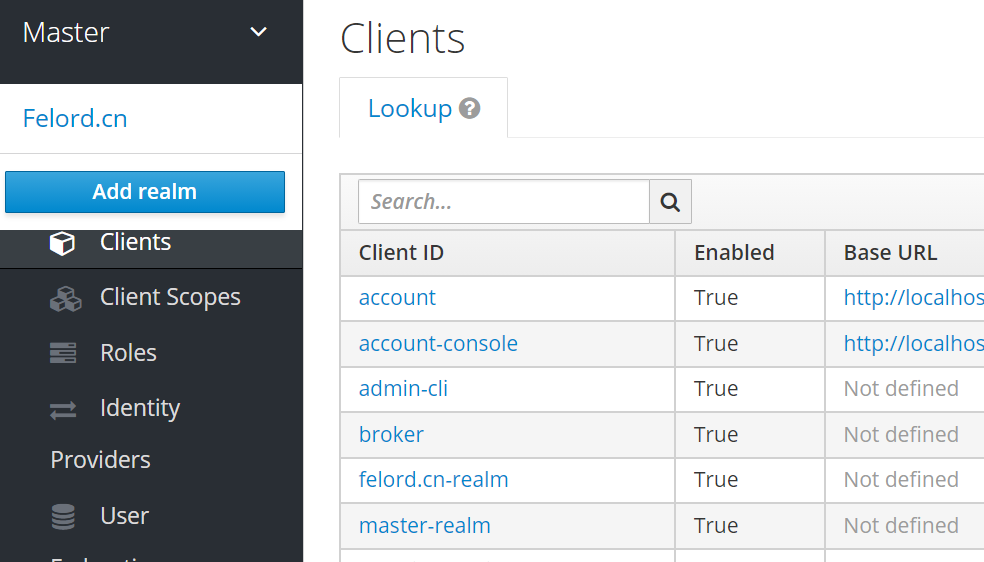
And you will find two roles unique to the users created in Master Realm that can be given to them.
- admin Super Administrator, with full access to manage any realm on the Keycloak server.
- create realm With this role you can create realm and get full administrative rights to that realm.
Recommended Master Realm is used to manage other Realm without being involved in specific operations.
Other Realm
Other Realm is a Realm created with Master, it is very easy to create other Realm, it can be created by the administrator of Master Realm. There are some options to configure if you create it successfully, but usually the default configuration is sufficient.
Setting up the Realm admin account
There are two ways to create a separate administrator account for the Realm felord.cn that I initialized earlier.
Manage with Master user
We create a user in Master Realm and strip the admin and create-realm roles in its role mapping, and check felord.cn-realm in Client Roles to give all the roles of that client to the created user. Example.
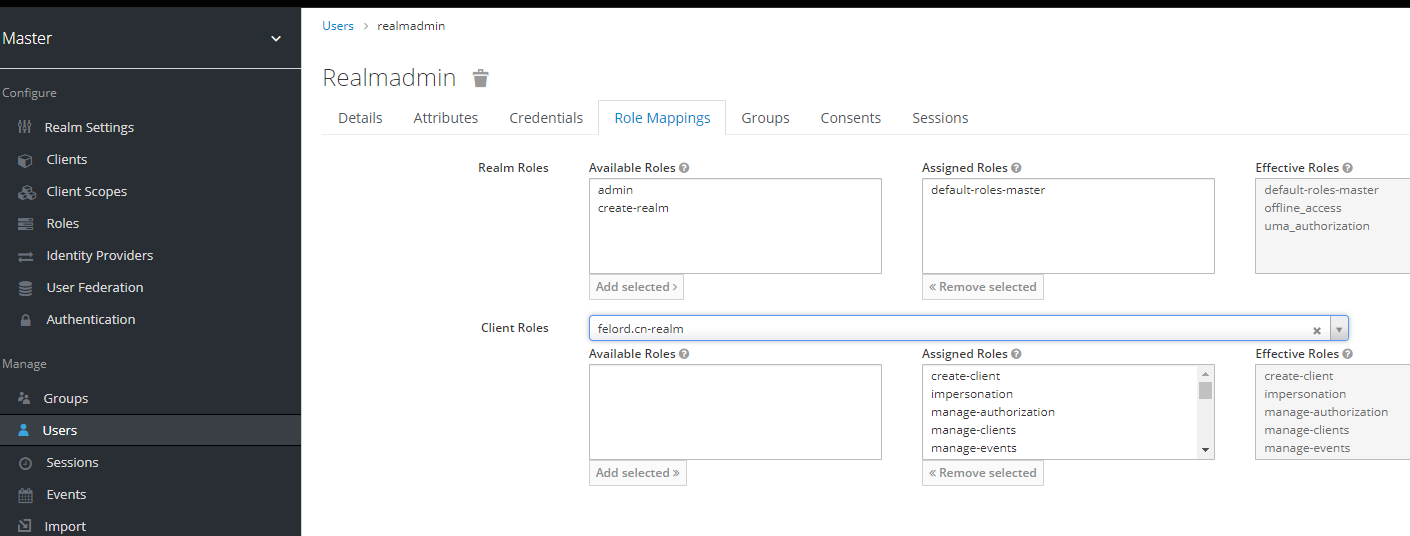
This user is a Master user, but manages the felord.cn Realm, which you can manage from the console using the link in the following format.
|
|
Using domain client user management
Another way is to create a user under the felord.co.uk domain and assign all client roles of its client realm-management to this user. This user belongs to felord.cn and can therefore only log into the administration console to manage the realm via the following link
|
|
A user can only be subordinate to one Realm.
Extensions
Keycloak Admin Client is a client tool for managing Realm through API operations, which I have already introduced in the previous article. Combining some of the concepts in this article may give you a deeper understanding of how to manipulate and manage Realm.
Reference
https://felord.cn/keycloak7.html