Entry
http://localhost:8082/oauth2/authorization/gitee
Suppose the request URL above is the starting point for the client to perform third-party authentication, the default format is {baseUrl}/oauth2/authorization/{clientRegistrationId}, where clientRegistrationId represents a third-party identifier, which can be WeChat, Alipay and other open platforms. Alipay and other open platforms, in this case gitee. After the user clicks on the request, the authorization journey begins. Spring Security must have intercepted the /oauth2/authorization before enabling the OAuth2 related processing logic. So let’s start here and explore from the source code. The IDEA shortcut CTRL SHIFT R will allow you to search globally for results.
Not surprisingly, I found three places, so I’ll write them down and look at them one by one!
OAuth2AuthorizationRequestRedirectWebFilter
First look at the first OAuth2AuthorizationRequestRedirectWebFilter, which implements Spring Webflux’s WebFilter interface, which is obviously a Webflux thing, and this will be useful if you use Webflux, but not what we use now.
DefaultOAuth2AuthorizationRequestResolver
The second is what it is, from the name looks like a default OAuth2 authorization request parser. Sometimes the name is a good way to know what this thing generally do, I have to say that the details of the excellent framework is very well designed. It implements the interface OAuth2AuthorizationRequestResolver .
|
|
This means that when we request /oauth2/authorization, DefaultOAuth2AuthorizationRequestResolver will extract the data from the oauth2/authorization corresponding HttpServletRequest and wrap it in the OAuth2AuthorizationRequest request object for further use.
NOTE:
/oauth2/authorizationis also customizable as the default interception identifier.
OAuth2AuthorizationRequest
Here it is briefly mentioned that OAuth2AuthorizationRequest encapsulates some of the OAuth2 related conceptual parameters we described in the previous article, which we will use in the subsequent request classes.
|
|
OAuth2AuthorizationRequestRedirectFilter
This was the only clue left, as soon as I saw that it inherited from OncePerRequestFilter I knew it had to be him. Even its member variables contain the OAuth2AuthorizationRequestResolver that is used to parse OAuth2 requests. Here we are on the right track and start analyzing this filter. Here is its core filtering logic, which is the logic we want to know how OAuth2 authorization requests are intercepted and processed.
|
|
The corresponding flow of doFilterInternal is as follows.
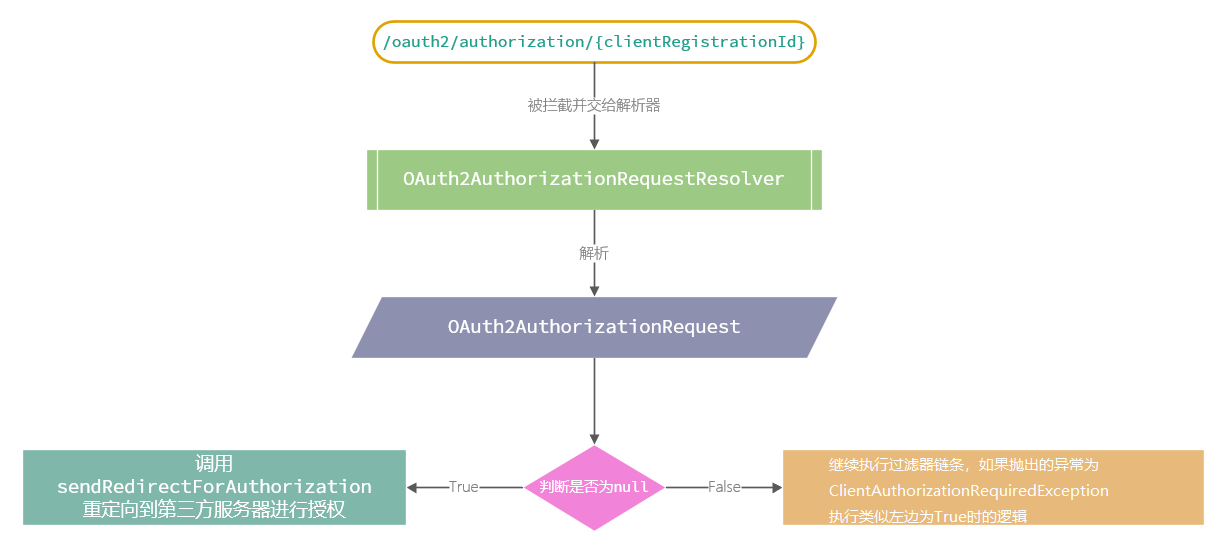
Based on this process, if you want to understand how Spring Security OAuth2 redirects to third parties, you need to delve into the sendRedirectForAuthorization method, which I will analyze in the next post for space reasons.
Summary
Today, we found the source of OAuth2 authorization processing portal step by step, and initially analyzed the role of several key components and the core interceptor interception logic. We will then go deeper and deeper to figure out its operation process step by step.