OIDC is an authentication layer based on OAuth2, so that the client knows the authorized End User, and provides a user’s authentication information Id Token while the client gets access_token. Widely used in microservices, open platforms, SSO, three-party login authorization and other scenarios.
OIDC key terms
- EU Abbreviation for End User, which refers to an end user.
- RP Abbreviation for Relying Party, which refers to the trusted client in OAuth2, the consumer of authentication and authorization information.
- OP Abbreviation for OpenID Provider, which refers to a service that has the ability to provide EU authentication (such as the authorization service in OAuth2) and is used to provide EU authentication information to the RP.
For other terms, see the list of OIDC terms.
OIDC Protocol Cluster
OIDC contains a number of specifications, the smallest of which is OIDC Core, the diagram below is an older one and is a bit out of date, but it will help you understand OIDC to some extent.
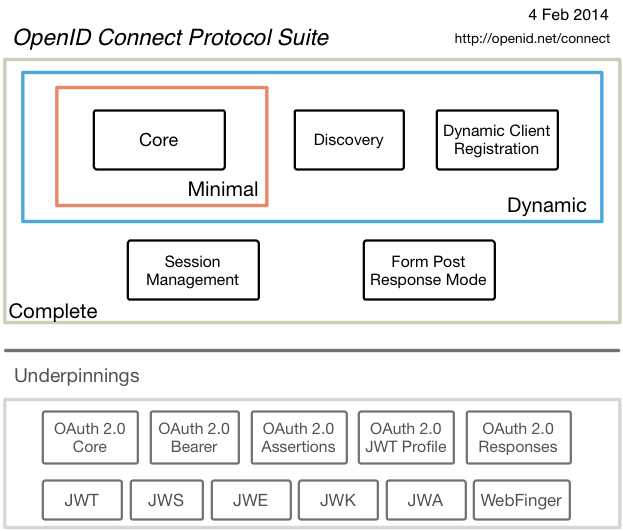
- Core OIDC Core, defines the core process of OIDC, how to authenticate on OAuth 2.0 and use declarations to communicate information about the end user (EU).
- Discovery defines how clients can dynamically discover information about OpenID Providers (OPs).
- Dynamic Registration Defines how a client can dynamically register to an OpenID provider.
- OAuth 2.0 Multiple Response Types defines several specific new OAuth 2.0 response types.
- OAuth 2.0 Form Post Response Mode defines how OAuth 2.0 authorization response parameters (including OpenID Connect authentication response parameters) are returned via the User Agent using the HTML form values automatically submitted by HTTP POST.
- RP-Initiated Logout Defines how the RP requests to OP to exit an EU.
- Session Management Session management, used to standardize how the OIDC service manages Session information.
- Front-Channel Logout A front-end based logout mechanism that enables the RP to logout without using the OP’s iframe.
- Back-Channel Logout A back-end based logout mechanism that defines how logout is done through interaction between RP and OP.
- OpenID Connect Federation Federation authentication, defines how OP and RP sets can establish trust by using a federation operator.
- Initiating User Registration via OpenID Connect defines the
prompt=createauthentication request parameter.
Two Web-based RP Implementation Guides
- Basic Client Implementer’s Guide A simple subset of the core functionality of Web-based RP using OAuth2 authorization code flow.
- Implicit Client Implementer’s Guide A simple subset of the core functionality of Web-based RP using OAuth2 steganography.
Migration Specification
- OpenID 2.0 to OpenID Connect Migration 1.0 OpenID Authentication 2.0 is a popular federated authentication protocol, OpenID Connect is a new version of OpenID Authentication and this specification defines how to migrate to the new OpenID Connect is a new version of OpenID Authentication, and the specification defines how to migrate to the new OpenID Connect.
There are still some drafts in the process of incubation, so I won’t go into them here.
OIDC Core Process
OIDC is abstracted into the following 5 steps, as shown in the figure.
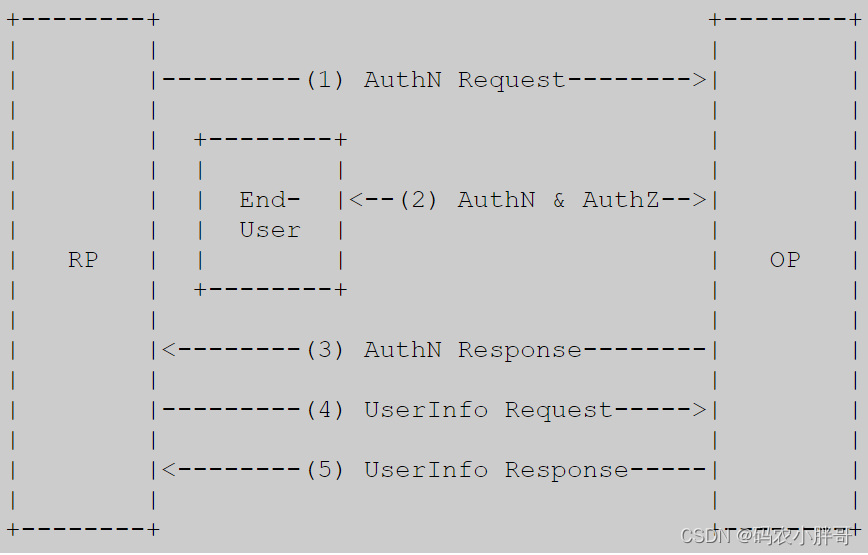
- RP (client) sends a request to OpenID provider (OP).
- OP authenticates the end user and obtains authorization.
- OP responds with an ID token, usually an access token.
- RP can send requests with access tokens to UserInfo endpoints.
- UserInfo endpoints return claims about the end user.
In contrast to OAuth2, RP is the OAuth2 client, where the request sent is not an authorization request, but an authentication (AuthN) request; OP is also the OAuth2 authorization server, which needs to provide EU (resource owner) claims and an authentication token Id Token on top of the OAuth2.
The OIDC authentication authorization process must include the authorization scope
openid.
Id Token
An Id Token is a concept specific to OIDC, which is a JWT token containing user information (claims), as follows.
|
|
Let’s take a look at the decoding of both the header and payload sections.
Head:
The header contains the regular JWT Header information and is compliant with the JOSE specification.
Payload:
From the above, the payload contains a series of claims, which have the following meanings.
The JWT specification defines seven reserved claims that are not required, but are recommended to allow interoperability with third-party applications. These are:
iss(issuer): Issuer of the JWTsub(subject): Subject of the JWT (the user)aud(audience): Recipient for which the JWT is intendedexp(expiration time): Time after which the JWT expiresnbf(not before time): Time before which the JWT must not be accepted for processingiat(issued at time): Time at which the JWT was issued; can be used to determine age of the JWTjti(JWT ID): Unique identifier; can be used to prevent the JWT from being replayed (allows a token to be used only once)You can see a full list of reserved claims at the IANA JSON Web Token Claims Registry.
How to perform OIDC authentication
The authentication flow of OIDC is mainly extended by several authorization flows of OAuth2, there are three kinds as follows.
- Authorization Code Flow based on OAuth2 authorization code flow for OIDC authentication authorization
Implicit Flowis based on the OAuth2 implicit flow, since OAuth2.1 removed the implicit flow, this should be removed as well.- Hybrid Flow is based on a hybrid flow of the above two, and should also be removed.
The reason why there is no client credentials pattern is that client credentials are designed to be used for interaction between clients and End User has nothing to do with it. So the focus is on Authorization Code Flow.
Please note that OIDC must use JWT as the token style.
User Information Endpoint
OIDC also provides the User Information endpoint, which is a resource endpoint. It is requested as follows.
|
|
It can also be a POST request. The basic return values are as follows.
If you also want to return user information such as email address, avatar, nickname, real name, etc., you need to carry an additional scope.
Summary
There is a lot more to OIDC, beginners can just master the basic functions above, for more features you need to refer to the official OIDC documentation. OIDC is much more versatile than the native OAuth2, it is a completely open standard and is compatible with some other IDP protocols.